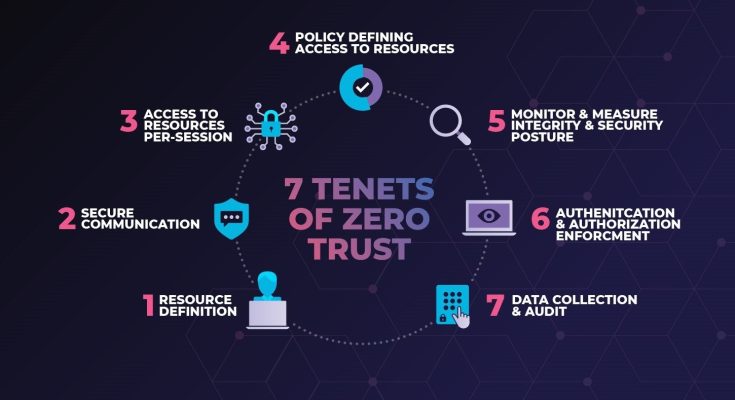
The Zero Trust security model represents a fundamental shift in how organizations think about cybersecurity. Rather than assuming that everything inside a network perimeter is trustworthy, Zero Trust operates on the principle that no user, device, or system should be trusted by default—regardless of whether it’s inside or outside the corporate firewall. This approach is rooted in the reality of today’s digital landscape, where remote work, cloud computing, and increasingly sophisticated cyber threats have rendered traditional perimeter-based defenses insufficient. Zero Trust is not a single product or technology but a strategic framework that guides how access is granted, monitored, and managed across an organization’s digital ecosystem.
At the heart of Zero Trust is the idea of continuous verification. Instead of granting broad access based on a one-time authentication, users and devices are constantly evaluated based on context, behavior, and risk. This means that even after a user logs in, their actions are monitored to ensure they align with expected patterns. If anomalies are detected—such as accessing sensitive data at an unusual time or from an unfamiliar location—the system can trigger additional authentication steps or restrict access altogether. This dynamic approach helps prevent lateral movement within networks, which is a common tactic used by attackers once they’ve breached initial defenses.
Implementing a Zero Trust model requires a granular understanding of who is accessing what, when, and why. Identity and access management becomes central to this strategy, with organizations adopting tools that enforce least privilege principles. Users are granted only the permissions necessary to perform their tasks, and those permissions are regularly reviewed and adjusted. For example, a contractor working on a short-term project might receive limited access to specific files and applications, with that access automatically revoked once the project ends. This minimizes the risk of unauthorized access and reduces the attack surface.
Device security also plays a critical role in Zero Trust. Organizations must ensure that endpoints—whether laptops, smartphones, or IoT devices—meet security standards before they’re allowed to connect to corporate resources. This might involve checking for updated antivirus software, verifying encryption settings, or assessing the device’s compliance with company policies. If a device fails to meet these criteria, it can be quarantined or denied access until the issues are resolved. This ensures that compromised or vulnerable devices don’t become entry points for attackers.
Network segmentation is another key component. By dividing the network into smaller, isolated zones, organizations can control traffic flow and limit the impact of potential breaches. If an attacker gains access to one segment, they won’t automatically have access to the entire network. This containment strategy is particularly effective in environments with sensitive data or critical infrastructure. For instance, a hospital might segment its patient records system from its administrative network, ensuring that even if one area is compromised, the other remains protected.
Visibility and analytics are essential for maintaining a Zero Trust posture. Organizations must be able to monitor activity across users, devices, and applications in real time. This involves collecting and analyzing logs, detecting anomalies, and responding to incidents swiftly. Advanced threat detection tools, powered by machine learning, can help identify subtle signs of compromise that might otherwise go unnoticed. By continuously analyzing behavior and context, these systems support proactive defense and enable rapid response to emerging threats.
Transitioning to a Zero Trust model is not a one-time project—it’s an ongoing journey that requires cultural and operational changes. It demands collaboration across IT, security, and business units to define access policies, implement controls, and educate users. Leadership must champion the initiative, emphasizing that security is a shared responsibility. Employees need to understand why certain measures are in place, such as multi-factor authentication or restricted access, and how their actions contribute to the organization’s overall security posture.
The benefits of Zero Trust are substantial. By reducing implicit trust and enforcing strict access controls, organizations can better protect against insider threats, credential theft, and advanced persistent attacks. It also supports compliance with regulatory frameworks that require robust data protection and access management. In a world where breaches are not a matter of if but when, Zero Trust provides a resilient foundation that limits damage and accelerates recovery.
Real-world examples illustrate the model’s effectiveness. When a global enterprise adopted Zero Trust principles, it was able to detect and contain a ransomware attack before it spread across the network. By segmenting systems and enforcing strict access policies, the organization minimized disruption and avoided significant financial loss. Similarly, a government agency used Zero Trust to secure remote access for employees during a rapid shift to telework, ensuring that only verified users and devices could connect to sensitive systems.
Ultimately, the Zero Trust security model reflects a pragmatic understanding of modern threats. It acknowledges that trust must be earned and continuously validated, not assumed. As organizations navigate an increasingly complex digital environment, Zero Trust offers a strategic path forward—one that prioritizes security, adaptability, and resilience. It’s not just a technical framework; it’s a mindset that aligns with the realities of today’s interconnected world.