In our increasingly digital world, personal data has become an invaluable commodity, a digital fingerprint that defines our online identities, fuels personalized experiences, and facilitates global commerce. However, this omnipresence of data also makes it a prime target for malicious actors. Cyber attacks, ranging from sophisticated phishing schemes to elaborate ransomware operations, are a constant and evolving threat, aiming to compromise sensitive information for financial gain, identity theft, or even geopolitical advantage. Protecting your personal data is no longer an option but a critical responsibility, demanding proactive measures and continuous vigilance in an interconnected society like that in Thailand, where digital transactions are now commonplace.
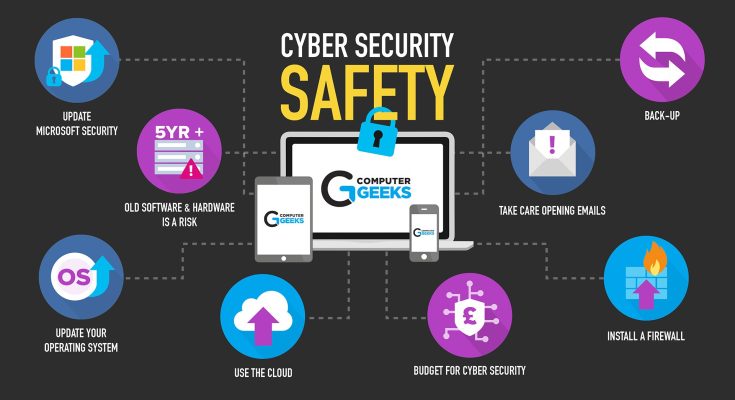
The first and most fundamental line of defense against cyber attacks is **strong password hygiene and multi-factor authentication (MFA)**. In an age where data breaches are unfortunately common, the weakest link often remains the human element. Reusing passwords across multiple accounts is akin to using the same key for every lock you own; if one lock is picked, all your defenses crumble. Instead, cultivate a habit of creating unique, complex passwords for every online service, combining a mix of uppercase and lowercase letters, numbers, and special characters, ideally at least 12-14 characters long. Given the difficulty of remembering such an array of distinct credentials, a reputable **password manager** is an indispensable tool. These applications securely store encrypted passwords, often generating strong ones for you, requiring you to remember only one master password. Complementing strong passwords with **multi-factor authentication (MFA)** adds a crucial layer of security. MFA requires a second form of verification beyond your password, such as a code sent to your mobile phone, a biometric scan (fingerprint or face ID), or a hardware token. Even if a cybercriminal manages to steal your password, they cannot access your account without this second factor, significantly increasing the effort required for a breach.
Beyond credentials, understanding and mitigating the risks posed by **phishing and social engineering attacks** is paramount. These attacks manipulate individuals into divulging sensitive information or performing actions that compromise their security, often by impersonating trusted entities. Phishing emails, for instance, might appear to be from your bank, a government agency (such as Thailand’s Ministry of Finance), or a popular online service, urging you to click a malicious link or download an infected attachment. Always exercise extreme caution with unsolicited emails, text messages, or phone calls. Look for red flags such as generic greetings, grammatical errors, suspicious sender addresses, or a sense of urgency designed to bypass critical thinking. If an email or message seems suspicious, do not click on any links or open attachments. Instead, navigate directly to the official website of the supposed sender by typing the URL yourself or use a trusted app. Remember, legitimate organizations will rarely ask for sensitive personal information like passwords or bank details via email.
Maintaining **software and operating system updates** is another non-negotiable aspect of data protection. Software developers regularly release updates that not only introduce new features but, crucially, patch security vulnerabilities that cybercriminals exploit. Running outdated software is like leaving a back door open for attackers. Enable automatic updates for your operating system (Windows, macOS, iOS, Android), web browsers, antivirus software, and all applications. This ensures your devices are always equipped with the latest security defenses, closing known loopholes before they can be exploited. This is particularly relevant for mobile devices, which store a wealth of personal data and are frequently targeted.
Furthermore, be incredibly mindful of your **internet connectivity, especially when using public Wi-Fi**. Public Wi-Fi networks in coffee shops, airports, or hotels are often unsecured, making it easy for cybercriminals to intercept your data, monitor your online activity, or even inject malware onto your device (known as a Man-in-the-Middle attack). Avoid conducting sensitive transactions, such as online banking or shopping, when connected to public Wi-Fi. If you must use public Wi-Fi, consider using a **Virtual Private Network (VPN)**. A VPN encrypts your internet connection, creating a secure tunnel for your data, making it unreadable to anyone trying to intercept it. Moreover, be cautious of public charging stations; some might be compromised to install malware or steal data (“juice jacking”). Always use your own charger plugged directly into a wall outlet or a trusted power bank.
Finally, a comprehensive data protection strategy includes **regular data backups and exercising caution with information sharing**. While preventative measures are crucial, a robust backup strategy ensures that even if your data is compromised by ransomware or a device failure, you can restore your important files. Employ the “3-2-1 rule”: keep at least three copies of your data, store them on two different types of media (e.g., external hard drive and cloud storage), and keep one copy off-site. Additionally, be judicious about what personal information you share online, particularly on social media. Over-sharing details about your life, travel plans, or even answers to common security questions can provide cybercriminals with valuable information for identity theft or targeted social engineering attacks. Review your privacy settings on all social media platforms and limit who can see your posts and personal information. In Thailand, the Personal Data Protection Act (PDPA) also empowers individuals with rights over their data, making it important to understand how organizations collect and use your information and to exercise your right to consent and access.
In conclusion, protecting your personal data from cyber attacks is an ongoing commitment in our hyper-connected world. It requires a multi-layered approach that combines strong technical safeguards with vigilant personal habits. By prioritizing robust passwords and MFA, recognizing and avoiding phishing attempts, keeping software updated, being cautious about network security, and practicing smart data management, individuals can significantly reduce their vulnerability to cyber threats. In an era where digital security is synonymous with personal security, taking these proactive steps is not just a recommendation but a necessity for safeguarding your digital life and maintaining peace of mind.